iOS Credential Phishing 'Flaw' Not Limited to Malicious Apps
Earlier today I came across a post by iOS developer Felix Krause who demonstrated a phishing vector within iOS; whereby, the iTunes login modal can be easily imitated by a malicious app.
This discovery is similar to the Google Docs phishing attack earlier this year. While this isn't necessarily a direct flaw within iOS, the attack vector is subtle and I bet would fool many people. In fact, I would be surprised if this wasn't previously used in the wild for a targeted spear phishing campaign. (Edit: It appears that this flaw was uncovered back in 2015!)
When I saw Felix's proof of concept, the first thing I thought is that this can also be leveraged in a web browser; no app or Apple App Store approval needed. I spent about 30 - 45 minutes and was able to create a pretty close replica of the iOS login dialog using pure HTML/CSS, and for the modal popup effect a few lines of javascript. Since this was just a proof of concept I didn't want to belabor the work, but I bet with an additional hour it could be made be look pixel perfect. Javascript and CSS3 effects could handle the transitions to make it appear like it's part of the native the native iOS UI.
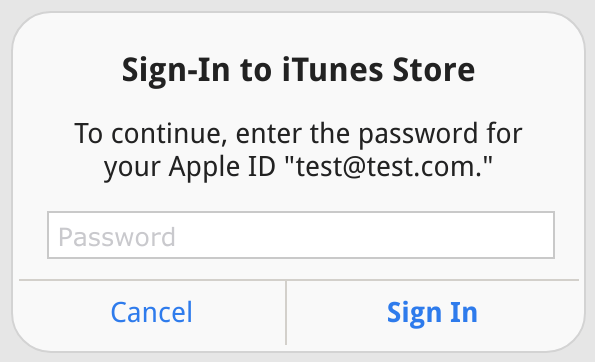
If an attacker combined this with an XSS flaw, the result could be subtle. Combined with a CSRF flaw, it might even be possible to identify the user's email address to place within the dialog.
Like Felix, I'm not going to release the code that creates the modal popup. You will need to spend a half hour of your own time doing that.
What to do about this? As always, be careful plugging your password in any box that pops up on your machine. What might be done within iOS? An indication of a system popup outside the app/browser window may help, perhaps by changing the navigation bar a different color. A better idea is to look toward Android and manage logins within an Accounts interface located within the system settings. Â That will ultimately need to be a decision by the iOS dev team.
Posted: Oct 10, 2017
Keyword tags: securityhackingphishing
Recent Posts:
Popular Posts:
Recent Security Posts:
S3 Buckets: Now With Both Leak & Fill Vulnerability
Stealing Data With CSS: Attack and Defense
Move Over S3: Open Directory Indexes Continue to be a Problem
Security Researchers Lose a Favorite DNS Recon Tool Jan 2018
KRACK: How To Protect Yourself on a Flawed Network
Equifax, SEC, & Now Deloitte: Organizations Must Employ Offensive Security
